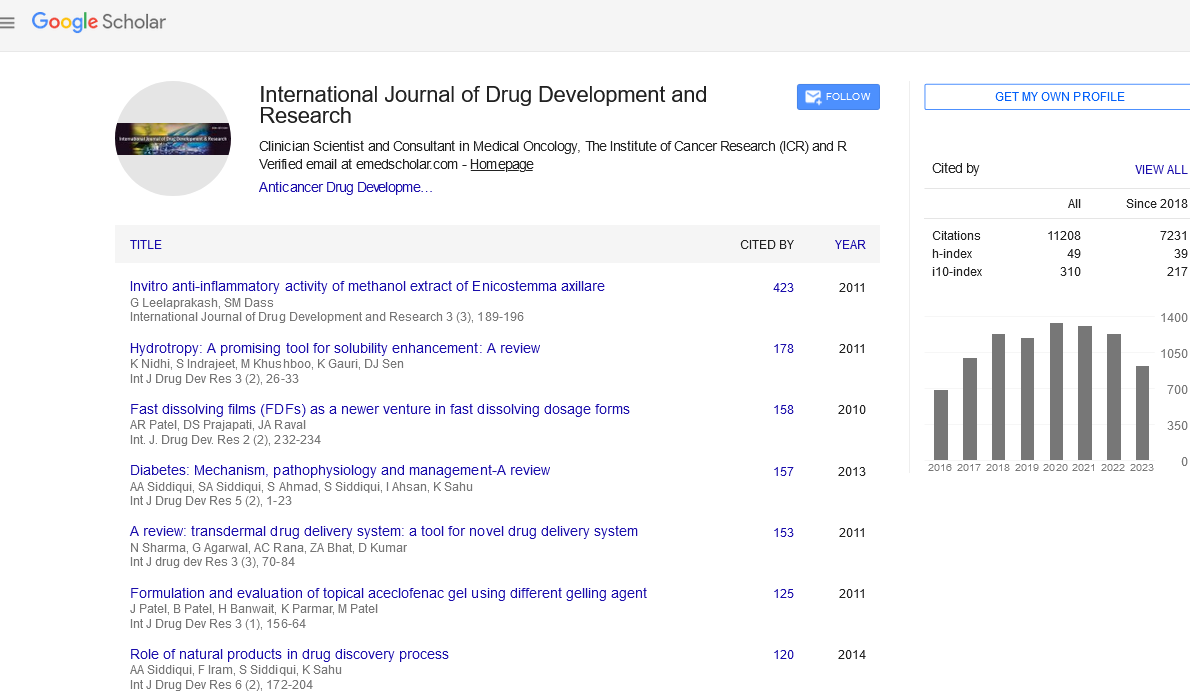
Keywords:
|
| counterfeit, tamper-evident, barcodes, holograms. |
INTRODUCTION:
|
| COUNTERFEIT: |
| According to WHO definition [1] “A counterfeit pharmaceuticals product are that is deliberately and fraudulently mislabelled with respect to identity or source. Counterfeit products may include products with correct ingredients, wrong ingredients, without active Ingredients, with the incorrect quantity of active ingredient or with fake packaging” [2]. |
| TAMPER-EVIDENT: |
| A package or container that is tamper-evident is made so that you can see if someone has opened it before it is sold in the shop. Tampering involves the deliberate altering or adulteration of information, a product, a package, or system. |
| Solutions may involve all phases of product production, distribution, logistics, sale, and use. Tamper-evident designs have been a feature of letters since ancient times, often using wax seals to signify that the letter had not been opened since it was written. Roman signet rings for example, were unique to the person who owned them, and the ring was pressed into the hot wax seal forming a signature which could not be easily duplicated by somebody attempting to re-seal the letter. |
DISCUSSION:
|
| Types of Counterfeit mechanism: |
| There are five different types of counterfeit mechanisms in which drugs are manufactured or distributed without proper regulatory approval and do not meet the determined standards of safety, quality, and efficacy: |
| 1. No active ingredient (43 %) |
| 2. Poor quality drugs (24 %) |
| 3. Low levels of active ingredient (21 %) |
| 4. Wrong ingredients (2 %) |
| 5. Wrong packaging or source (7 %) [3] |
| COUNTERFEITING OF DRUGS IN INDIA: |
| According to a report by the Organization for Economic Co-operation and Development, 75% of fake drugs supplied world over have origins in India, followed by 7% from Egypt and 6% from China[4] [Figure 1]. |
| Methodology: |
| Anti-counterfeit packaging includes following techniques [5] |
| 1. Serialisation/track and trace technologies |
| 1.1. Barcodes |
| 1.2 Radio frequency identification (RFID) |
| 2. Overt Technologies |
| 2.1 Holography |
| 2.2 Colour shifting security inks and films |
| 2.3 Security graphics |
| 2.4 Sequential product numbering |
| 2.5 On-product numbering |
| 3. Covert Technologies |
| 3.1 Invisible printing |
| 3.2 Embedded images |
| 3.3 Digital watermarks |
| 3.4 Anti-copy or anti scan design |
| 3.5 Laser codes |
| 1. Serialisation/track and TRACK AND Trace technologies |
| A number of track and trace applications are under development for the pharmaceutical sector, although the principles have been established for many years in other contexts. These involve assigning a unique identity to each stock unit during manufacture. |
| 1.1 BARCODES: |
| Barcodes are used in the pharmaceutical industry to identify product throughout the supply chain. Different levels of information can be carried in a barcode, including such items as National Drug Code (NDC), Lot Number, and Expiration Date [5]. |
| 2-D Barcodes are present in following formats [Figure 2]. |
| A. Linear format |
| B. Scripted format |
| C. 2-D data matrix format |
| 1.2 RADIOFREQUENCY IDENTIFICATION (RFID): |
| RFID is a wireless data collection technology that uses radio signals for identifying objects. The basic premise behind RFID systems is that you mark items with tags. These tags contain transponders that emit messages readable by specialized RFID readers. Most RFID tags store some sort of identification number; for example a customer number or product SKU (stock?keeping unit) code. A reader retrieves information about the ID number from a database, and acts upon it accordingly and list of companies using this technology is as shown in [6] [Table1]. |
| Medicines have been the centre of attraction for the counterfeiters to the number of reasons listed in [Table2] and the factors responsible for the counterfeiting are shown in [Figure 3]. Maximum counterfeit reports are related to antibiotics, antiprotozoal, hormones and steroids. |
| 2. Overt Technologies: |
| Overt features enable instant authentication of packaging through visual inspection by the user without requiring expert knowledge. Optically variable features such as holographic devices within the design and colour shift inks are the most common and effective overt security features, enabling packaging to be validated both quickly and easily. |
| 2.1. Holographyq |
| Easily identifiable holograms, showing the pharmaceutical manufacturer's logo for example, are primarily used as first level identification devices and are designed to enable successful authentication at point of inspection. Additional features, such as Nano text and hidden images, can be used as second and third level techniques for trained and equipped specialists. |
| 2.2. Colour shifting security inks |
| Colour shift inks appear as two or more distinct colours when viewed from differing viewing angles. Such features are easily verified by tilting the item carrying the colour-shift in order that the different colours can be seen. Different colour combinations are available and both strong opaque and subtle transparent effects can be created to complement the existing design of the packaging. |
| Currently, only a limited number of security suppliers produce colour-shift inks since the process to create the colour-shift pigment is highly specialized requiring particular technical knowledge and bespoke equipment. Supply of colour-shift inks is tightly controlled to ensure that the products are used only in genuine circumstances and under strict codes of conduct including end use agreements [9]. |
| 2.3. Security graphics |
| Fine line colour printing, similar to banknote printing, incorporating a range of overt and covert design elements such as guilloches, line modulation and line emboss. They may be used as background in a discrete zone such as an overt print area, or as complete pack graphics, and can be printed by normal offset lithography, or for increased security by intaglio printing. Subtle use of pastel ”spot” colours makes the design more difficult to scan and reproduce, and security id further enhanced by the incorporation of a range of covert design elements, such as micro text and latent images [10]. |
| 2.4. Sequential product numbering |
| Unique sequential numbering of each pack or label in a batch can make counterfeits easier to detect in the supply chain. If printed visibly, it provides a semi-overt means of authentication by reference to a secure database, because duplicates or invalid numbers will be rejected. The main disadvantages of sequential numbering are that the sequence is predictable and easily replicated, and end users require some means of access to the database. The more secure option is serialisation by means of a pseudo-random nonrepeating sequence, and this is discussed in the track and trace section [11]. |
| 2.5. On-product Marking |
| On-product marking technologies allow for special images or codes to be placed on conventional oral dosage forms. These overt technologies can be difficult to replicate and offer a security technology at the pill level. This added layer of security is effective even when products are separated from the original package. |
| 3. COVERT (Hidden) Features: |
| The purpose of a covert features is to enable the brand owner to identify counterfeited product. |
| 3.1 Invisible printing |
| Using special inks, invisible markings can be printed on almost any substrate, and which only appear under certain conditions, such as via UV or IR illumination. They can be formulated to show different colours with illumination at different wavelengths. |
| 3.2 Embedded image |
| An invisible images can be embedded within the pack graphics which can only be viewed using a special filter, and cannot be reproduced by normal scanning means. The effects can be quite dramatic and well hidden. |
| 3.3 Digital watermarks |
| Invisible data can be digitally encoded within graphics elements and verified by means of a reader and special software. The data can be captured using webcam, mobile phone or other scanning equipment, but the information is not visible to the human eye, and attempts to replicate it will be detected by virtue of the degradation of the embedded data. |
| 3.4 Hidden marks and printing |
| Special marks and print may be applied in such a way that escapes attention and is not easy to copy. Their effectiveness relies on a combination of secrecy and subtlety, and hence no further details will be discussed here. |
| 3.5 Anti –copy or Anti-scan design |
| Fine line background patterns appear as uniform tones, but when scanned or copied reveal a latentimages which was not previously visible. Commonly used on secure documents to prevent photocopying, the may be applied to product packaging as a background tint. |
| 3.6 Laser coding |
| 4. FORENSIC MARKERS |
| There is a wide range of high technology solutions which require laboratory testing or dedicated field test kits to scientifically prove authenticity. These are strictly a sub-set of covert technologies, but the difference lies in the scientific methodology require for authentication. |
| 4.1 Biological taggants |
| A biological marker can be incorporated at extremely low levels (parts per million or lower) in product formulations or coatings, or invisible applied to packaging components. At such low levels they are undetectable by normal analytical methods, and require highly specific “lock and key” reagent kits to authenticate [12]. |
| 4.2 Micro taggants |
| Micro taggants are microscopic particles containing coded information to uniquely identify each variant by examination under a microscope. This may take the form of alphanumerical data depicted on small flakes or threads, or of fragments of multi-coloured, multi-layered laminates with a signature colour combination. These can be embedded into adhesives, or directly applied to packaging components as spots or threads. |
| TAMPER-EVIDENT FEATURES]: |
| Tamper-evident packaging may involve container or primary pack systems or any combination thereof. |
| Note: Sealed paperboard cartons such as those sealed by gluing the end flaps and / or side-seam together are not an acceptable form of tamperevident packaging [13]. |
| i. Film wrappers – transparent |
| A transparent film with distinctive design is wrapped securely around the entire product container ensuring the product is completely sealed and a secure tight fit is achieved. The wrapper must be ripped or broken to gain access to the product [Figure 4]. |
| ii. Blister or strip packs |
| Individual doses (for example, capsules or tablets) are sealed in plastic and/or foil. Blister or strip pack seals around individual compartments and the strip as a whole, must be intact and complete. vi. HEAT SHRINK BANDS OR WRAPPERS Bands or wrappers with a distinctive design are shrunk by heat to tightly seal the union of the cap and container. |
| The seal must be ripped or broken to gain access to the product. The wrapper cannot be removed and reapplied without visible damage [Figure 9]. |
| vii. Container mouth inner seals |
| Paper, thermal plastic, polystyrene foam, plastic film, foil, or combinations thereof, with a distinctive design is sealed to the mouth of a container under the cap. The seal must be broken to open the container and gain access to the product. The seals cannot be removed without showing visible evidence of entry, and once removed, seals cannot be reapplied without showing visible evidence of entry [Figure 10]. |
| viii. Breakable caps |
| The plastic or metal cap has a portion that breaks away on opening and remains on the neck of the container. |
| The cap cannot be removed or reapplied in its original state [Figure 11]. |
| ix. Tear-away caps |
| The plastic or metal caps has a portion that is torn away in order to allow the remains on the remainder of the cap to be removed to gain access to the product. The tear away portion must be clearly torn or missing once the package is opened. The cap cannot be removed or reapplied in its original state [Figure 11]. |
| x. Sealed metal tubes |
| The nozzle is blocked by seal or membrane. The nozzle seal must be broken or punctured to gain access to the product [Figure 12]. |
| xi. Sealed plastic/ laminate tubes |
| The lower end of the tubes is sealed by heat sealing and crimping. That end must not be capable of being breached without visible evidence of entry. |
| The nozzle is blocked by a seal, membrane or twist off top and must be broken or punctured to gain access to the product [16] [Figure 13]. |
| xii. Heat shrink bands or wrappers |
| A band or wrapper is securely applied to a portion of the container, usually at the juncture of the cap and container. The band or wrapper is heat shrunk to provide a tight fit. The band or wrapper must be cut or torn to open the container and remove the product and cannot be worked off and reapplied without visible damage. The use of a perforated tear strip can enhance tamperresistance. Cellulose wet shrink seals are not acceptable [17-20]. |
| The knowledge to remove and reapply these seals without evidence of tampering is widespread. The band or wrapper must employ an identifying characteristic that cannot be readily duplicated. An identifying characteristic that is proprietary and different for each product size is recommended. Tinted bands or wrappers are no longer acceptable as an identifying characteristic because of the possibility that their material or a facsimile may be available to the public. |
CONCLUSION:
|
| To protect from counterfeit medicines patients have to check it. Now a day’s pharmaceutical companies are using various anti?counterfeit packaging as barcodes, holograms. There is chance to make duplicate copies of these packaging. Covert (invisible to naked eye) security features provide higher security compared to overt (visible) ones. Hence pharmaceutical companies may use modern anti?counterfeit techniques as RFID to track and trace pharmaceutical products. |
Tables at a glance
|
 |
 |
 |
 |
| Table 1 |
Table 2 |
Table 3 |
Table 4 |
|
| |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
 |
 |
 |
 |
 |
| Figure 6 |
Figure 7 |
Figure 8 |
Figure 9 |
Figure 10 |
 |
 |
 |
| Figure 11 |
Figure 12 |
Figure 13 |
|
| |